Assessing audit and logging configurations
Logs are files that detail all the events that occur within the cloud. Logs can show deviations from expected activity, giving visibility of potential security issues. Different log types include application, server, access, network logs, and so on. Logging is a practice that enables you to collect and correlate log data from cloud applications, services, and infrastructure. It is performed to help identify issues, measure performance, and optimize configurations. Logging is a valuable tool for security analysis, as it can help an organization maintain an audit trail of transactions performed in the cloud.
The three cloud providers; AWS, Azure, and Google Cloud Platform (GCP) provide native tools for logging. AWS provides AWS CloudTrail and Amazon CloudWatch Logs, Azure provides Azure Monitor Logs while GCP offers Cloud Logging. This is not an exhaustive list, but some of the key tools that are used for audit and logging. Let’s look at the three cloud providers in detail.
AWS
Two services that can be leveraged in tandem by the IT auditor are Amazon CloudWatch Logs and AWS CloudTrail. Amazon CloudWatch Logs furnishes logs in a unified flow of events ordered by time. On the other hand, AWS CloudTrail is a service that logs actions performed in an AWS environment.
Amazon CloudWatch Logs
To launch Amazon CloudWatch Logs, perform the following steps:
- Navigate to the AWS portal.
- Search for CloudWatch.
- Navigate to CloudWatch | Logs | Logs Insights | History.
As shown in Figure 10.1, you can interactively query and analyze your log data in Amazon CloudWatch Logs:
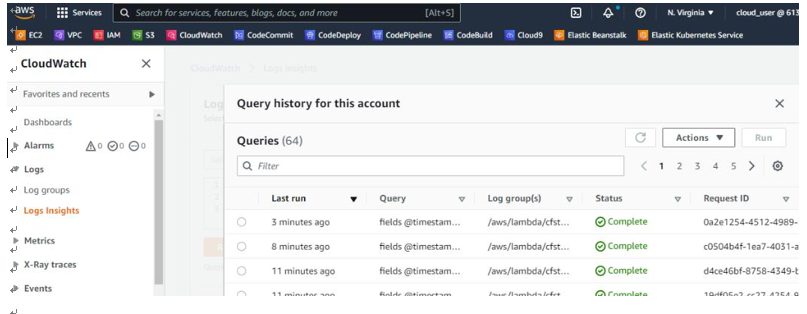
Figure 10.1 – Amazon CloudWatch Logs | Logs Insights
AWS CloudTrail
To launch AWS CloudTrail, take the following steps:
- Navigate to the AWS portal.
- Search for CloudTrail.
- Navigate to CloudTrail | Event history.
As shown in Figure 10.2, you can see a user named cloud_user has created and modified attributes of a virtual private cloud (VPC). This might be useful information foran IT auditor:
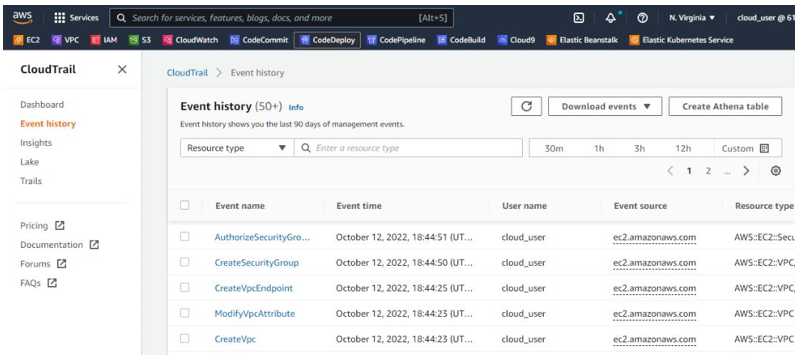
Figure 10.2 – AWS CloudWatch Logs | Event history
Now that we have looked at logging and auditing tools in AWS, let us look at the tools an IT auditor can leverage in Microsoft Azure.
Microsoft Azure
Within Microsoft Azure, we’ll belooking at Azure Monitor. Azure Monitor aggregates and correlates data across Azure cloud resources.
Azure Monitor
Within Azure Monitor, there is an Activity Log feature that provides insight into cloud events. The activity log includes information such as when a resource is created or modified.
To launch Activity Log within Azure Monitor, take the following steps:
- Navigate to the Microsoft Azure portal.
- Select Monitor | Activity log.
As shown in Figure 10.3, the IT auditor can review what operations have been performed. We can see a virtual machine was created. During an assessment, an IT auditor could inquire whether cloud_user_p_58a8eb is authorized to create or make changes to infrastructure:
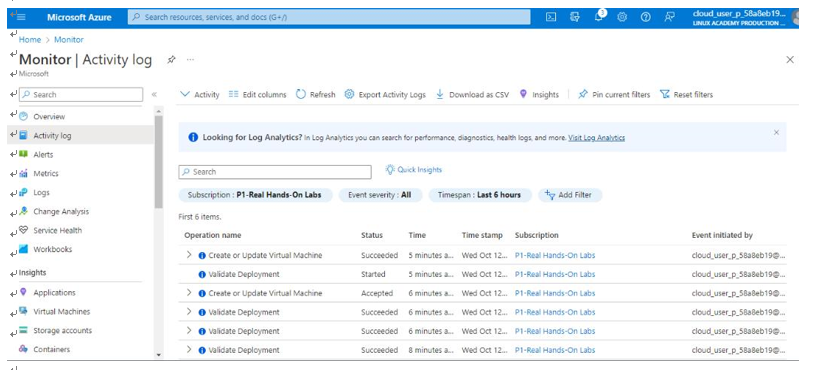
Figure 10.3 – Azure Monitor | Activity log
Another useful feature in Azure Monitor is Change Analysis. Change Analysis detects various types of changes, from the infrastructure layer through application deployment, as seen in Figure 10.4:
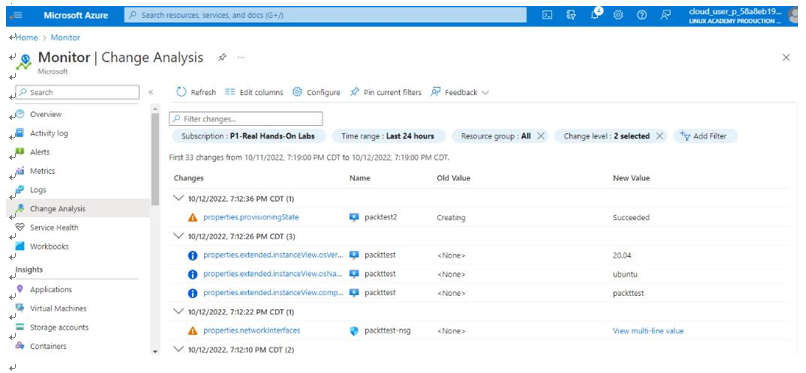
Figure 10.4 – Azure Monitor | Change Analysis
Now that we have looked at logging and auditing tools in Azure, let us look at tools an IT auditor can leverage in GCP.
GCP
Under GCP, we’ll be looking at Cloud Logging. Google Cloud Logging provides log data that you can use to gain insights into GCP.
Cloud Logging
Logs Explorer is a feature in Google Cloud Logging that can be used to retrieve, view, and analyze log data.
To launch Logs Explorer within Cloud Logging, take the following steps:
- Navigate to the Google Cloud portal.
- Select Logging | Logs Explorer.
As shown in Figure 10.5, the Logs Explorer interface lets you query resource log data using resource types such as VM Instance, GCE Firewall Rule, and GCE Network:
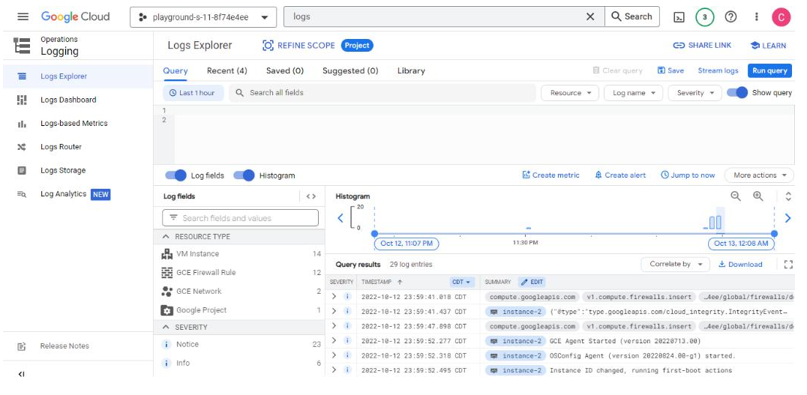
Figure 10.5 – GCP Logs Explorer
Now that we have performed a walk-through of basic audit and logging configurations let’s look at assessing change management and configuration policies.