Assessing device controls
In our last walk-through session for IAM controls, let’s look at assessing a common control related to devices – the configuration of multi-factor authentication (MFA). In our sample walk-through, we will validate whether MFA is being enforced for all users and their devices in our AWS and Microsoft Azure cloud environments.
AWS IAM
In the previous section on assessing privileged access controls, we saw that AWS provides a Users report within the Identity and Access Management (IAM) service. As shown in Figure 8.16, we can see that MFA requirements for individual users can be found here. In the screenshot, we can see that the user is not enrolled in or required to use MFA, which would mean the control test fails in this instance:
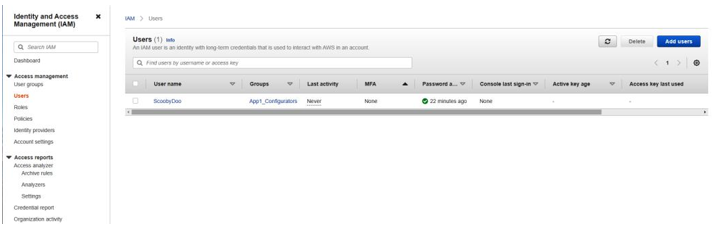
Figure 8.16 – The AWS IAM Users report column selection
Another way to see the same information is within the credential report, which we reviewed in the section on assessing authentication and authorization controls. As shown in Figure 8.17, the report includes a field that indicates whether MFA is active for each user, providing an easy way to sort and determine whether the control objective is met:
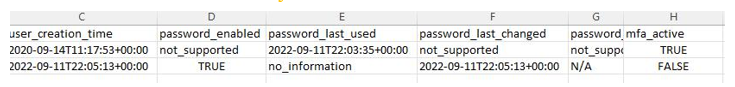
Figure 8.17 – The AWS IAM Users report column selection
Now that we’ve seen how some of the previous testing procedures in AWS can also help in assessing device controls such as MFA, let’s take a look at reviewing MFA controls within Microsoft Azure.
Microsoft Azure
As we’ve covered throughout this book, there are often many paths within cloud environments to get to the same information, and reviewing device controls and compliance within Microsoft Azure is no different. One way that we can test that there are no exceptions to device control policies such as MFA would be to take the following steps:
- Navigate and log in to the Microsoft Azure portal.
- Navigate to Azure Active Directory.
- Navigate to the Devices blade.
As shown in Figure 8.18, the overview shows that there are no devices that are uncompliant with the device policy. However, we should investigate this a little further:
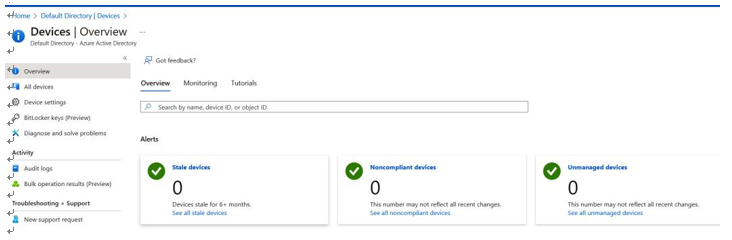
Figure 8.18 – Microsoft Azure Devices | Overview
Prior to accepting the content of Devices | Overview as evidence that there are no exceptions to the policy, let’s check what the policy is by looking at the Device settings blade. Here, as shown in Figure 8.19, we can now see that there may be exceptions that allow MFA to not be enforced uponcertain behaviors. This highlights why it is important for you as an auditor to understand not only what is being provided as test evidence but also how the specific cloud environment is configured to align with that test evidence.
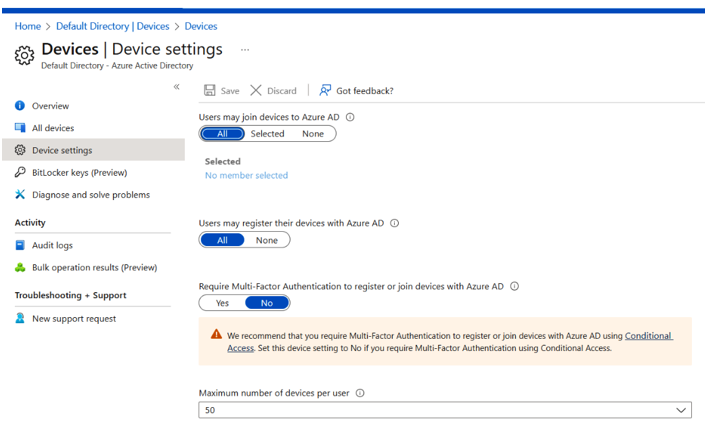
Figure 8.19 – Microsoft Azure Device settings
In this section, we’ve performed a simple walk-through of device MFA enforcement settings, and we are now aware that in addition to overview reports showing compliance, we need to dig deeper and assess what is in the compliance policies to confirm whether control objectives are being met.
Summary
In this chapter, we performed a walk-through of common and practical IT general computing controls that may be performed when auditing cloud environments. We covered steps to assess authentication and authorization and reviewed that in a multi-cloud environment, these controls should be tested in all clouds. We also performed an assessment of access assignment controls and executed steps to determine who has privileged access.
We finished this chapter by performing a walk -through of a device -related control (MFA) and saw the importance of understanding how relying on overview details as test results could prevent the detection of configuration that does not align with the control objectives.
In the next section, we’ll continue with our walk-throughs – this time assessing policy settings and resource controls.