Assessing privileged access controls
As an auditor, it’s important to understand who has been granted privileged access within an environment. Knowing who has been granted privileged access and whether that level of access is appropriate given the individual’s job responsibilities is often a foundational step before assessing other IT general computing controls.
AWS IAM
One primary way of identifying users in AWS that have privileged access is by reviewing which users have access keys and when those access keys were last used. To pull this evidence, you can perform the following steps:
- Navigate and log on to the AWS console.
- Select the Identity and Access Management (IAM) service.
- Select Users within the Access management option.
- Within the Users report, you can review and filter users by a given set of criteria. To ensure all relevant options are visible in the report, you will need to open Preferences and ensure the options related to privileged access are part of your visible column list; as shown in Figure 8.12, you will have the following options:
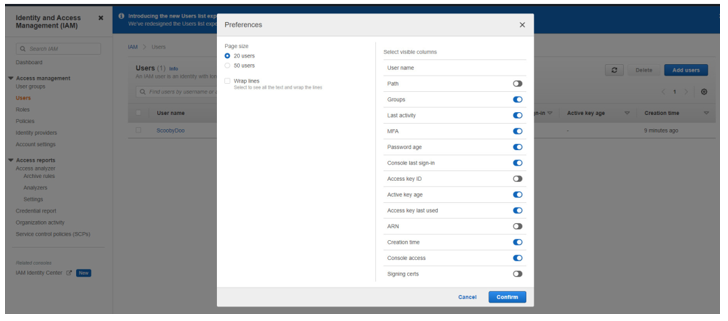
Figure 8.12 – AWS EC2 Users report column selection
Once we have this list of users with privileged access, we can compare this with the expected list of users. Keep in mind this gives us one method to view users with privileged access; however, this is not the only method. Depending upon the configuration of the enterprise cloud environment, additional steps may need to be taken to obtain all users with privileges with access to cloud services.
Now that we’ve seen one method for pulling a list of privileged users with AWS IAM, let’s look at an option for pulling a list within Microsoft Azure.
Microsoft Azure
To validate a list of privileged users within an Azure environment, we need to execute the following test steps to verify the assignment of privileged access:
- Navigate and log in to the Microsoft Azure portal.
- Navigate to Azure Active Directory.
- Navigate to the Roles and administrators blade.
As shown in Figure 8.13, when accessing the Roles and administrators blade, we have the option to select Download assignments. This will give us a comprehensive list of users with Azure Active Directory role assignments, from which we can validate the actual versus the expected list of users:
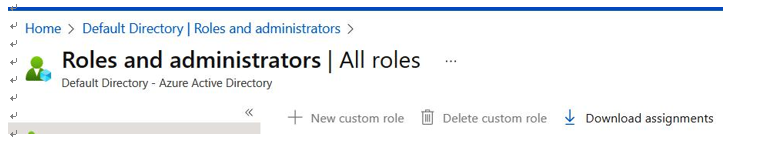
Figure 8.13 – The Microsoft Azure Roles and administrators blade
After selecting the Download assignments option, you then need to navigate to the Bulk operation results blade, as shown in Figure 8.14, to view and extract the report. A list of downloads that have been requested will be visible. To open the report, click on the entry under the Type column for the report that you wish to open:

Figure 8.14 – Microsoft Azure Roles and administrators bulk operation reports
Upon opening the report, as shown in Figure 8.15, you will find the role assignments (roleDisplayName) and users (displayName) to which they are assigned. You can also distinguish between built-in privileged roles (isBuiltIn) and the user type (objectType). Within this report, you can easily sort the specific privileged role assignments and see a list of users with this access. If you are unfamiliar with which built-in roles have privileged access, you can refer to the information shared in Chapter 3, Identity and Access Management Controls, on where to go for additional details.
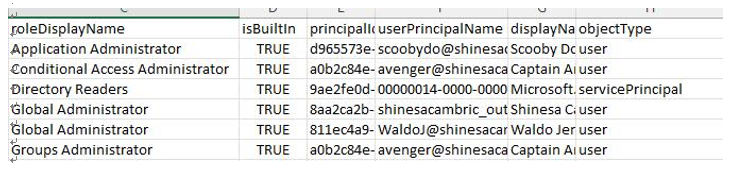
Figure 8.15 – The AWS EC2 Users report column selection
Now that we’ve done a walk-through of identifying privileged users, let’s take a look at assessing device controls within a couple of cloud environments.