Assessing resource management policies
Within cloud environments, there are several different types of resource controls. One type, the ability to manage billing and cost controls, not only has a financial impact but also has technical implications as well. In many cases, these controls may define a hierarchy of who can add additional compute resources, how those resources are provided, and the scale of those resources being allocated. Not managing this properly could lead to environmental sprawl and architecture that is not fully documented or vetted and to significant charges for resource consumption if effective controls are not in place. Additionally, in some cases, being defined as a billing administrator also provides a level of privileged technical access within the enterprise cloud environment, making this ability especially sensitive. Another type of resource control that we covered in Chapter 5, Financial Resources and Change Management, was the use of enabling policies, labels, and tags to control the management of resources.
In this walk-through, we will step through pulling resource adherence to compliance policies. In Azure, we will validate that all resources are compliant with the enabled policies, and in GCP, we will confirm the asset count of resources and that each is appropriately tagged and labeled to indicate use and sensitivity.
Microsoft Azure
To validate that our resources adhere to all enabled controls, we can execute the following test steps to confirm the automated controls that are applied and which our resources are compliant with:
- Navigate and log in to the Microsoft Azure portal.
- Navigate to Policy | Compliance.
- In the filters, select the relevant Scope.
As shown in Figure 9.3, there are some scopes for which the compliance checks have failed. The count of policies that did not pass can also be seen in the following figure:
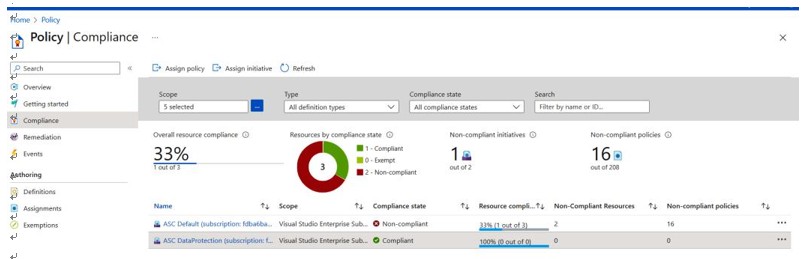
Figure 9.3 – Microsoft Azure compliance policies
When reviewing compliance policy adherence, note the second item in the list for which it shows 100% compliance, but the number of resources is 0. When we look at this further, as shown in Figure 9.4, we can see that in this instance, the scope does not contain any resources for which the assigned policies are relevant, and this may warrant further investigation regarding policies that have been applied:
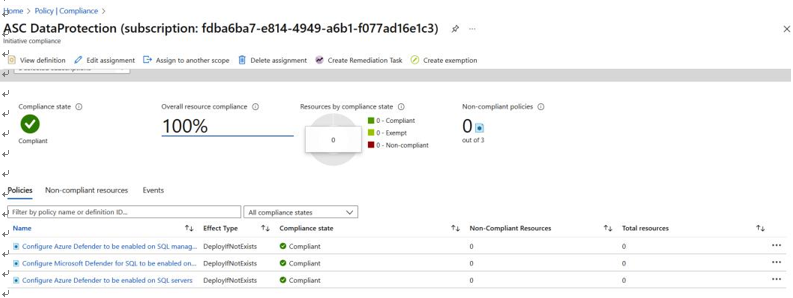
Figure 9.4 – Microsoft Azure compliance, no policies applied
Now that we’ve determined a method for verifying adherence to enabled policies within Microsoft Azure, let’s look at testing the resource asset inventory in GCP.
GCP
Within the GCP environment, to get a list of assets and confirm that labeling and tags have been applied, we can execute the following test steps:
- Navigate and log in to the Google Cloud console.
- Navigate to IAM & Admin | Asset Inventory.
As shown in Figure 9.5, you can see a list of assets associated with the GCP project. This list can be filtered to show only those that are enabled:
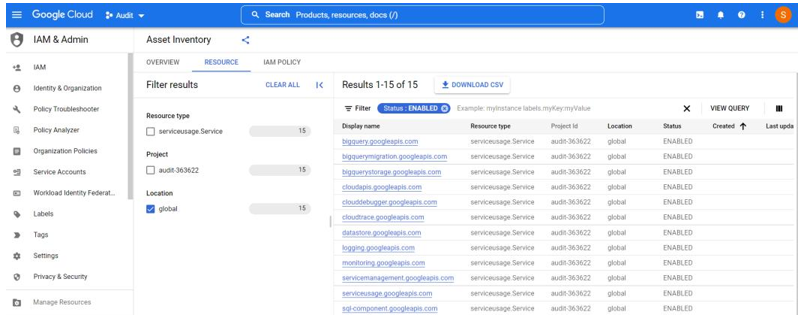
Figure 9.5 – GCP Asset Inventory
From this list, we can then determine a sample against which we can review whether labels and tags have been applied according to our enterprise control. To review the labels and tag information for our samples, we can filter our results and then download them to CSV format to see this information, as shown in Figure 9.6, or we can click on each entry within the GCP portal to see additional details:
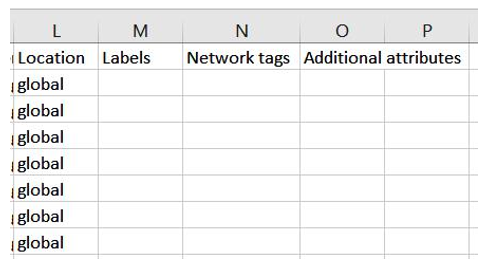
Figure 9.6 – GCP Asset Inventory labels and network tags
Now that we’ve covered some ways to assess basic controls related to resource management through policy applications (Azure) or tagging and labels (GCP), let’s look at performing an assessment of data security policy controls in AWS and Azure.