AWS IAM
In AWS, a convenient way to identify that users inactive for 180 days are disabled, is to execute the following test steps:
- Navigate and log in to the AWS console.
- Select the Identity and Access Management (IAM) service.
- Select Credential report.
- As shown in Figure 8.1, you will have the option to download this report locally. The downloaded report will provide you with a list of all users associated with the AWS instance and the status of their credentials, including the creation date and last login information:
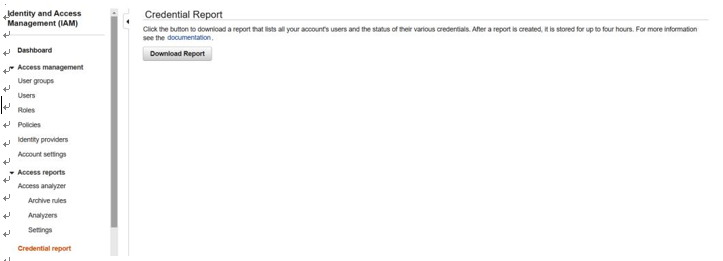
Figure 8.1 – AWS IAM Credential Report
Once you’ve downloaded and opened the report, depending on the scope of the audit and the size of the user population, you may need to extract a sample from the list. However, within the report, as shown in Figure 8.2, you will be able to see two pertinent columns for the control – user_creation_time and password_last_used. This will give you an indication of theage of the account and the period for which it has or hasn’t been active. Based on the accounts here, our testing shows this control passes for the AWS environment:
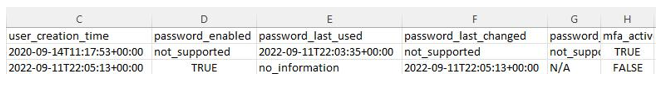
Figure 8.2 – AWS credential report download
Now that we’ve performed the control assessment within AWS IAM, let’s look at performing the same control assessment in Microsoft Azure.
Microsoft Azure
To validate the control requiring that users inactive for 180 days be disabled, you can execute the following test steps to get an initial sample:
- Navigate to the Microsoft Azure portal.
- Select Azure Active Directory.
- Navigate to the Users | All users blade.
Either select the option to filter users created within the last 360 days or edit the columns to include the Creation time field, as shown in Figure 8.3. If this is the first audit being conducted, you may want to go back further than 360 days for the user population:
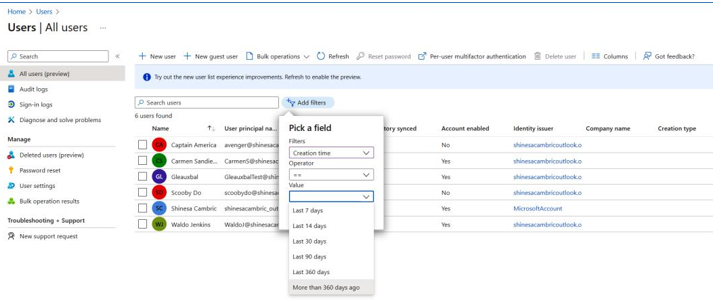
Figure 8.3 – Microsoft Azure user list
After identifying your sample population, you will want to compare this with sign-in details for those accounts. In this example, we have found that Carmen Sandiego, as shown in Figure 8.4, meets our sample selection criteria, so now let’s see if our inactivity control passes for these users:

Figure 8.4 – Microsoft Azure filtered user list
To review the sign-in details for the selected users, you can execute the following test steps:
- Navigate and log in to the Microsoft Azure portal.
- Navigate to Azure Active Directory.
- Navigate to the Users blade.
- Perform a search for one of the selected users by entering the display name in the search and then selecting that user by clicking on the hyperlinked display name. Here you will be able to view sign-in details or directly access the sign-in logs for the user, as shown in Figure 8.5:
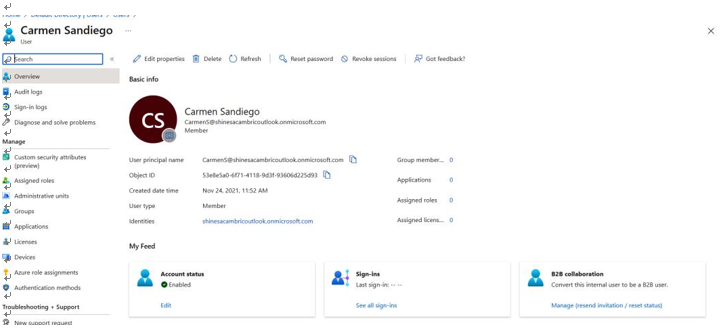
Figure 8.5 – Microsoft Azure selected user with sign-in details
Note that in our sample scenario, this control has failed. As shown in Figure 8.6 , this user has no recent sign- ins, and based on the user creation date, it is clear that the user has been inactive for greater than 180 days:
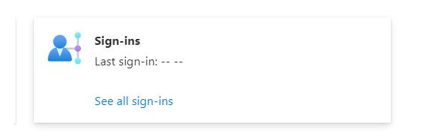
Figure 8.6 – Microsoft Azure user sign-in history
Based on the previous steps, we can say that there are easy methods for gathering evidence for some basic IT general computing controls within cloud environments. We’ve also demonstrated the importance of assessing the control in multiple cloud environments if the organization is using more than one cloud provider for operations.
Now that we have performed a walk-through of a typical authentication and authorization control, let’s look at assessing access assignment controls.