Azure Automation
Another tool that organizations use for change and configuration management is Azure Automation. Azure Automation allows an organization to automate changes in the Azure environment and across external systems.
You first need to create an Automation account before using Azure Automation.
To launch Azure Automation, use the following steps:
- Navigate to the Microsoft Azure portal.
- Select Automation.
A useful feature for an IT auditor under Configuration Management is Change tracking. Change tracking allows you to track infrastructure changes. The Overview tab can also provide a summary of the status of changes, as seen in Figure 10.11:
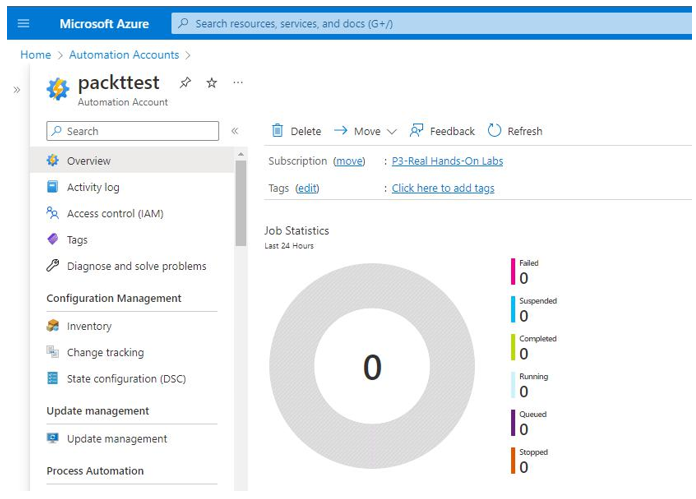
Figure 10.11 – Azure Automation Configuration Management | Change tracking
Another useful feature in Azure Automation is Activity log, as seen in Figure 10.12. Activity log displays the status of operations performed, as well as who initiated the event. This is very useful information for an IT auditor:
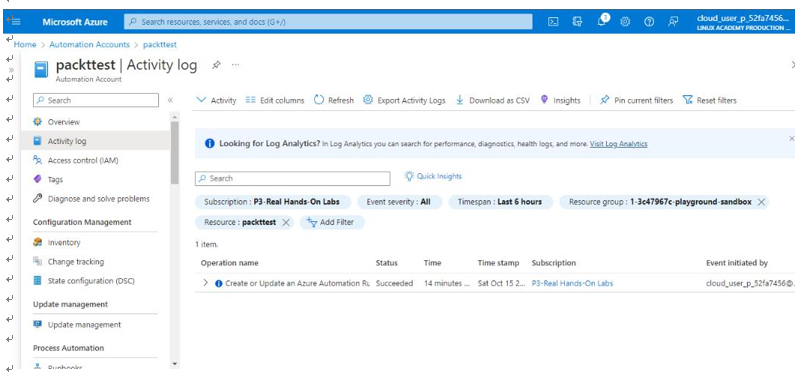
Figure 10.12 – Azure Automation | Activity log
Another tool that can be used to manage changes in the cloud is Terraform.
Terraform
Terraform is an open source, infrastructure as code (IaC) software created by HashiCorp. Many organizations utilize Terraform open source software (OSS) to help provision and configure infrastructure in the cloud. To be familiar with how an organization can use Terraform OSS to provision resources in AWS, we will provide an example. We first need to install various components, including Terraform OSS.
The first step in the Terraform workflow is to write your Terraform configuration. Here is a snippet of our sample code:
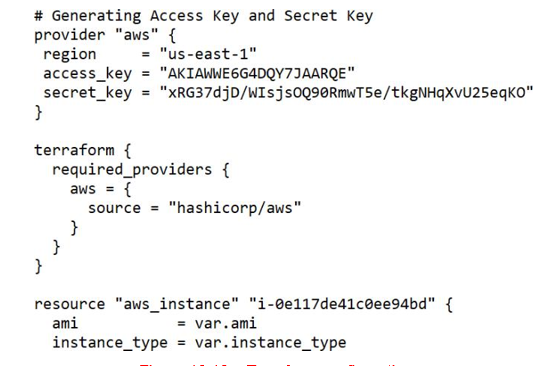
Figure 10.13 – Terraform configuration
The second step is to prepare the code for download by running the terraform init command.
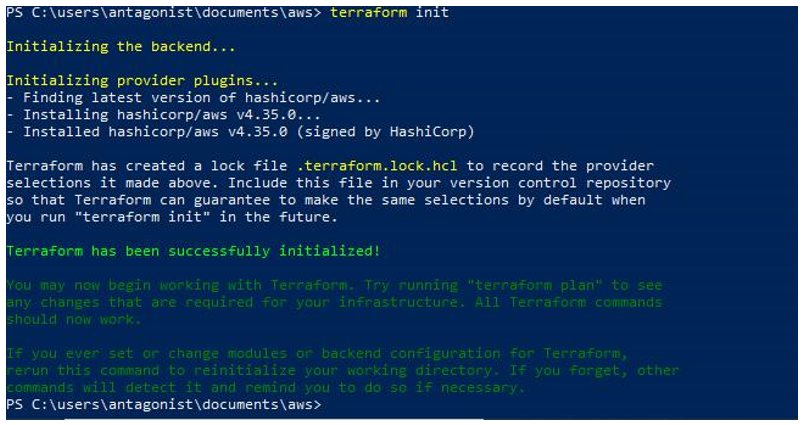
Figure 10.14 – The terraform init command
This command initializes the environment and downloads the AWS provider. The AWS provider is a plugin that Terraform relies on to interact with remote systems.
The third step is to review the changes using the terraform plan command, as seen in Figure 10.15.
This command creates an execution plan for the environment and confirms no bugs are found.

Figure 10.15 – The terraform plan command
The last step is to accept the changes and apply them against the organization’s infrastructure using the terraform apply command, as seen in Figure 10.16:
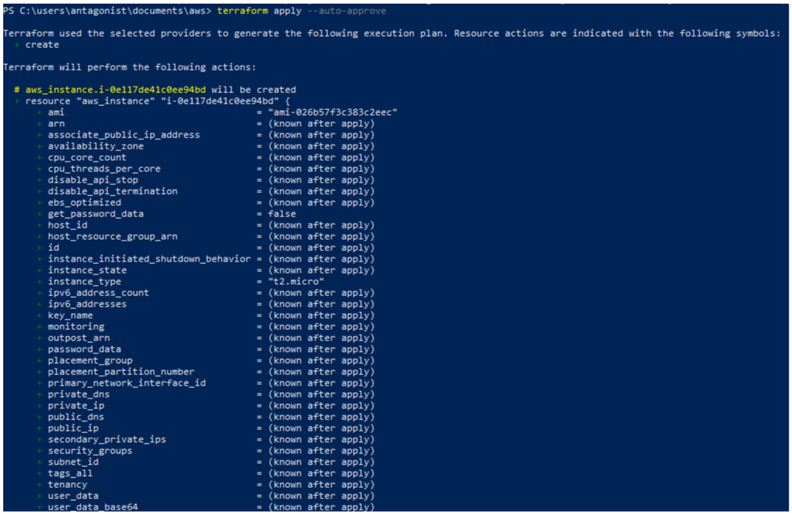
Figure 10.16 – The terraform apply command
One thing you should have noticed is that our Terraform code contains hardcoded credentials. Software developers with poor security practices often embed credentials into their code to save time during the code development process. This poses a security risk to the organization, as code containing credentials may then be inadvertently uploaded into a public repository service. In a real-life scenario, an IT auditor should document the hardcoded credentials as a finding.
An IT auditor can utilize Terraform Enterprise to monitor changes in an organization’s cloud. Once we have installed Terraform Enterprise, we will need to log in with an API token, as seen in Figure 10.17:

Figure 10.17 – Terraform Enterprise login with API token
Once logged in, the IT auditor can run some commands. One useful command is the following:
terraform graph
The terraform graph command is used to generate a visual representation of infrastructure defined in Terraform code in a diagram, as seen in Figure 10.18:
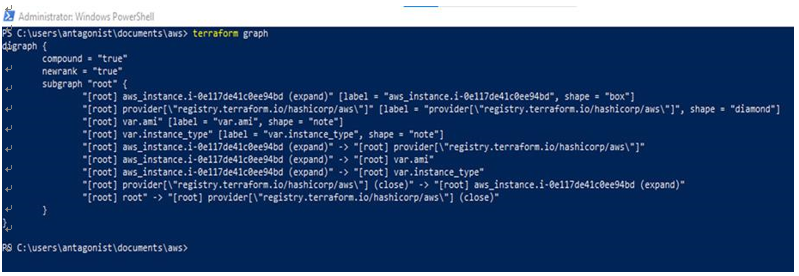
Figure 10.18 – The terraform graph command
You can use various utilities, such as graphviz, to output the graph. An example of a graph copied from the HashiCorp website can be seen in Figure 10.19. The graph is very useful to an IT auditor as it gives a representation of what the infrastructure environment looks like:
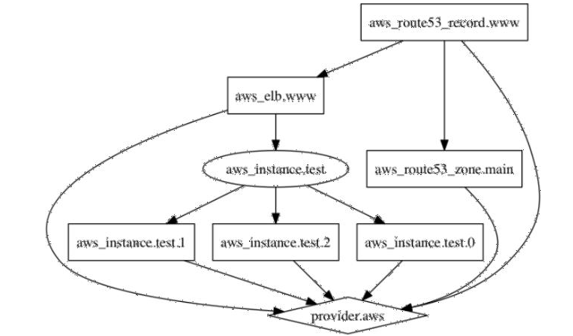
Figure 10.19 – Example of a Terraform graph output
In addition, Terraform Enterprise has another product named Sentinel. Sentinel contains the functionality to ensure an organization’s code against infrastructure aligns with specific policies. This idea is called Compliance as Code or Policy as Code.
Compliance as code refers to using software code for automating the implementation, validation, and management of the required compliance standards that an organization needs to be compliant with.
With compliance as code, controls and policies are agreed to and defined in a tool such as Sentinel. Sentinel constantly monitors the applications for changes. Any change is evaluated and checked according to the compliance rules. If Sentinel detects an application violating a compliance rule, it triggers another action or modifies the application back to a compliant state.
As an example of compliance as code, imagine a company that is subject to Payment Card Industry (PCI) regulations. One of the PCI regulations, Requirement 4, mandates an organization to protect cardholder data with strong cryptography during transmission over open, public networks. The organizationhas a standard to implement Transport Layer Security (TLS) 1.2 protocol or newer for data in transit, which is a strong cryptographic standard.
The organization can then write a policy in Sentinel that evaluates whether there are any protocols older than TLS 1.2 running on the organization’s systems. If a violation is found, Sentinel triggers an alert allowing for manual or automated remediation to occur. Next, let’s look at an open-source tool an IT auditor can leverage to assess identity changes.