Change history
As an auditor, one method that may be used to correlate processes and procedures that mitigate risk is to review activity logs. In cloud environments, these logs may be made up of separate sign-in and event logs that are capturing change history and actions performed by user accounts, service accounts, or workload identities.
In each of the cloud environments, you will find multiple options for tracking the activity that’s occurred. The amount of this activity that is tracked, where it is tracked, and for how long this information is made directly available will change based on licensing, cloud system configuration, and cloud provider. In some cases, supplementary data storage tools or platforms may need to be used to ensure longer retention that meets compliance requirements. As an IT auditor, you should also note that not all items are logged by default. In some cases, an organization may need to manually enable logging or the settings to log certain activities, and there may be a cost for doing so. An organization may have the assumption that the cloud provider has the default responsibility of logging activity and making logs available, but an organization should refer to the Shared Responsibility Model referenced in Chapter 1, Cloud Architecture and Navigation, as well as periodically review logging settings within their environments.
Change history is typically found in audit logs. Depending on the cloud provider and the event, the navigation to these logs could be dispersed throughout the environment. In Microsoft Azure, for example, you may need to search through audit logs, sign-in logs, log analytics, and provisioning logs, as well as enable diagnostics settings to use workbooks to further query log information. The ability to read these audit logs is tied to specific permissions, as shown in Figure 5.11:
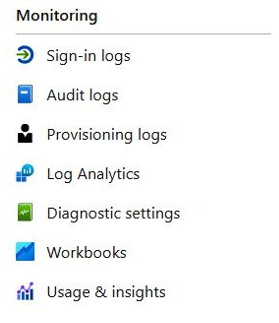
Figure 5.11 – Azure Monitoring
As part of assessing changes to a particular resource or object in a cloud environment, in some cases, it is possible to get the activity by selecting it and identifying its Activity log, as shown in Figure 5.12:
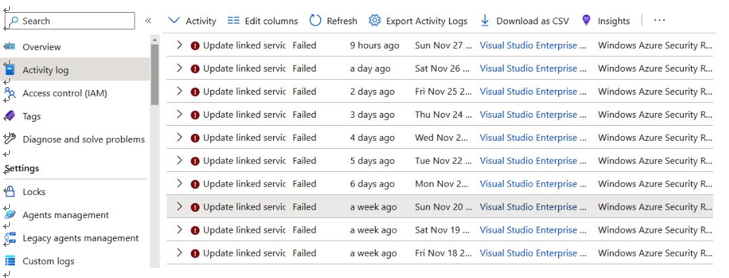
Figure 5.12 – Microsoft Azure Activity log for a resource
In AWS, an organization might use CloudTrail (as shown in Figure 5.13) to view event history, or they may be routing to an S3 bucket for storage or out to a third-party SIEM tool. And depending on the environment and control being tested, you may also need to ensure that Amazon network logs, known as VPC Flow Logs, are enabled and available. To find out more about VPC Flow Logs, go to https://docs.aws.amazon.com/vpc/latest/userguide/flow-logs.html.
As an IT auditor, it will be important to ask and understand all logging for all event types. Also, be aware that there may be significant cost implications to logging data and the methods used to retain those logs. This cost may impact the organization’s architecture and operational choices, also leading to new or additional risks being identified or controls being adopted. Leveraging cost monitoring and alerting, which will be covered later in this chapter, may be of increased importance in scenarios that require a high degree of logging:
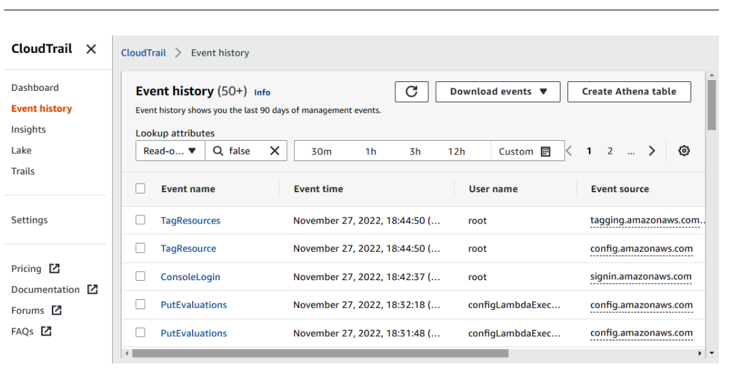
Figure 5.13 – AWS CloudTrail
In many GCP scenarios, logs are enabled by default, but that is not the case for every type of log. In Figure 5.14, we can see that for this Google Cloud environment, the log types for Data Access audit logs need to be explicitly selected:
Figure 5.14 – Google Cloud audit log configuration
As an IT auditor, understanding that this is configurable and reviewing who has the access to modify this configuration (and when this configuration is changed, where is it logged) should be an essential part of your audit program.
In Figure 5.15, we can see that the retention period for Log buckets varies by the log type and whether it is a default log versus what is determined as a required audit log:
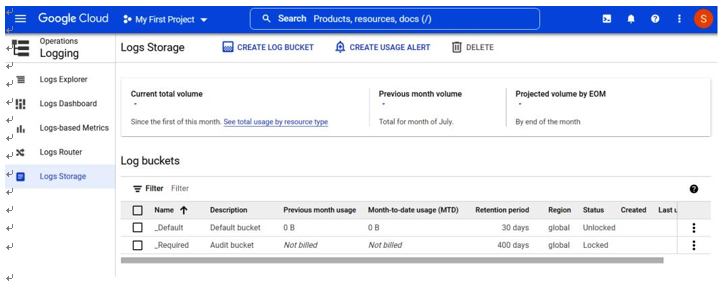
Figure 5.15 – Google Cloud audit log storage configuration
As we wrap up this section, the importance of making sure all pertinent logging is enabled and capturing all in-scope activities for the period required cannot be understated. More information on audit log options for each of the three providers can be found at the following links:
- AWS: https://docs.aws.amazon.com/whitepapers/latest/introduction-aws-security/monitoring-and-logging.html
- Microsoft Azure:https://learn.microsoft.com/en-us/azure/active-directory/reports-monitoring/
- GCP: https://cloud.google.com/logging/docs/audit/
Now that we’ve covered some important aspects of both managing change and reviewing change history, let’s look at billing and cost controls.