Google Cloud Platform Virtual Private Cloud
Similarly, for GCP, the following security policies related to networking in the CIS Google Cloud Platform are recommended:
- 3.1 Ensure that the Default Network Does Not Exist in a Project
- 3.2 Ensure Legacy Networks Do Not Exist for Older Projects
- 3.3 Ensure that DNSSEC is Enabled for Cloud DNS
- 3.4 Ensure that RSASHA1 is Not Used for the Key-Signing Key in Cloud DNS DNSSEC
- 3.5 Ensure that RSASHA1 is Not Used for the Zone-Signing Key in Cloud DNS DNSSEC
- 3.6 Ensure that SSH Access is Restricted From the Internet
- 3.7 Ensure that RDP Access Is Restricted From the Internet
- 3.8 Ensure that VPC Flow Logs are Enabled for Every Subnet in a VPC Network
- 3.9 Ensure No HTTPS or SSL Proxy Load Balancers Permit SSL Policies With Weak Cipher Suites
- 3.10 Use Identity Aware Proxy (IAP) to Ensure Only Traffic From Google IP Addresses are “Allowed”
For each control, the CIS benchmarks provide detailed instructions on why the policy is recommended, as well as the rationale. For example, for 3.1 Ensure that the Default Network Does Not Exist in a Project, it is recommended that “To prevent the use of default network, a project should not havea default network.” The rationale given is that “The default network has a preconfigured network configuration and automatically insecure firewall rules.”
With that, we’ve looked at how to implement industry-standard security benchmarks within security policies for each of the three cloud providers. Next, let’s look at security attributes we can apply to protect data within virtual networks in the cloud.
Data security
Cloud networks have public frontends and the ability to communicate with the broader internet. As we said earlier in this chapter, cloud infrastructure is exposed to the internet. As a result, it can be susceptible to attacks such as denial-of-service attacks, data exfiltration, and so on.
A denial-of-service attack is the act of flooding your network with tons of illegitimate network traffic to overload your network and prevent you from fulfilling the real requests. Data exfiltration is a type of security breach that leads to the unauthorized transfer of data. There are many attack paths an adversary can take once they have obtained some sort of access to a cloud network.
Securing networks running in the cloud is essential to providing data security. The following security controls can mitigate the risks presented by the cloud:
- Encryption: To protect data in transit, network traffic should be encrypted, regardless of whether the traffic goes over public networks or within a secure private network. Encryption should be implemented to avoid man-in-the-middle (MiTM) attacks. Network traffic should be encrypted using a secure protocol such as Transport Layer Security (TLS). The IT auditor should check that deprecated ciphers are not being used, such as TLS 1.0 or TLS 1.1. TLS 1.2 or above is encouraged. Another option is to encrypt data in cloud storage before it is transmitted so that it is secure as it travels from point A to B. For instance, you could enable Server Message Block (SMB) encryption for Azure VMs. SMB encryption provides end-to-end encryption of data. This would ensure the data is encrypted in transit as it travels over Azure VNets. In addition, the IT auditor should be cognizant of any organization using unsecure protocols such as Telnet or FTP.
- Firewalls: Firewalls separate trusted network traffic fromuntrusted. Use additional security solutions such as firewalls and WAFs to actively detect and block malicious traffic. A firewall should be placed at the edge of the network. WAFs will block connections at edge locations long before they can get onto your network. For example, in Azure VNets, you can enable a firewall. Navigate to Virtual network | Capabilities, as shown in Figure 4.37:
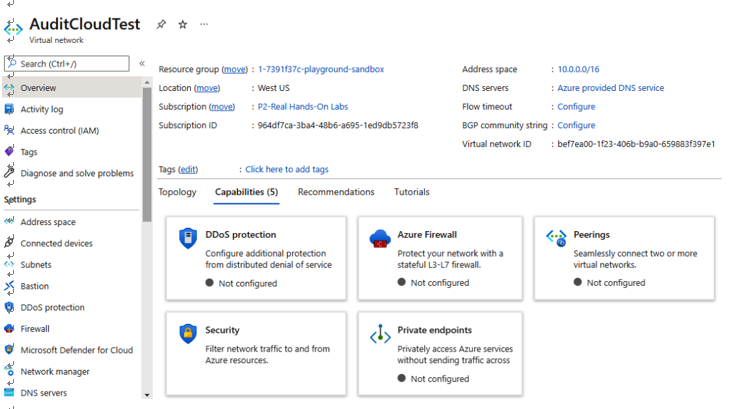
Figure 4.37 – Azure VNet – Capabilities
Navigate to Azure Firewall to either enable Azure Firewall or create a new firewall, as shown in Figure 4.38:
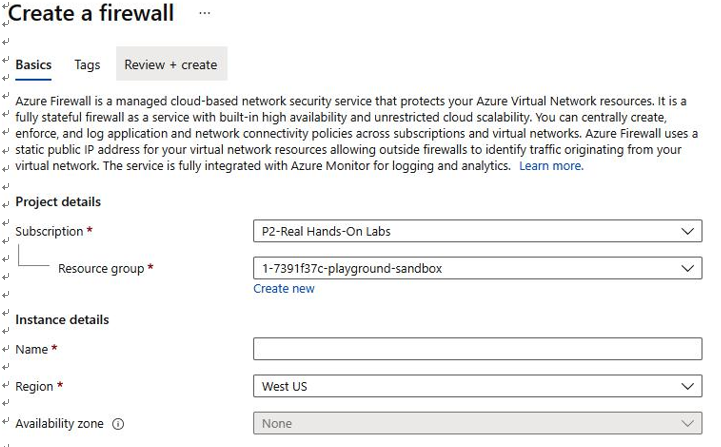
Figure 4.38 – Azure VNet – Create a firewall
In addition, you can navigate to DDos protection and enable the capability to mitigate denial-of-service attacks, as shown in Figure 4.39:
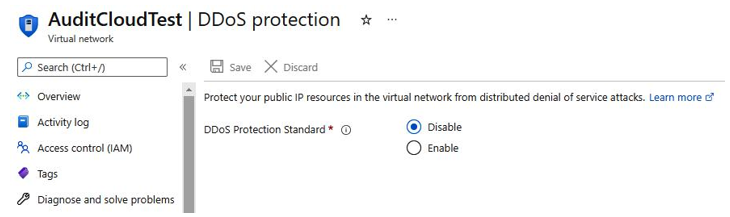
Figure 4.39 – Azure VNet – DDos protection
- Peering: Peering is a technique for securely connecting two or more virtual private clouds, or virtual networks. When peering is implemented, resources running in separate clouds can communicate with each other as if they were running on the same private network. Without peering, resources running in distinct clouds would have to communicate over the public internet, which would significantly increase their exposure to potential attack or abuse. Peering can help mitigate further risks of exploitation when data is transferred outside of the spaces you control, which is the internet. For example, in Azure, you can enable Peerings. Navigate to Virtual network | Capabilities, as shown in Figure 4.40:
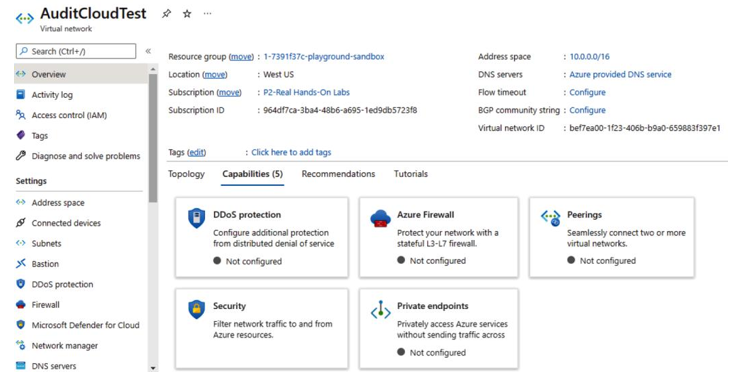
Figure 4.40 – Azure VNet – Peerings
Next, Add peering, as shown in Figure 4.41:
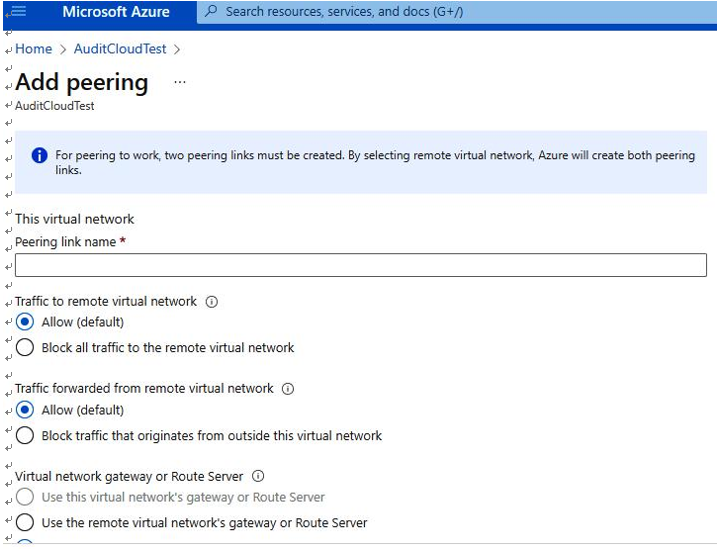
Figure 4.41 – Azure VNet – Add peering
- Network Address Translation Gateway: Also known as a NAT gateway, this is used to enable instances present in a private subnet to access the internet. In addition to this, the NAT gateway makes sure that the internet doesn’t initiate a connection with the instances. To prevent unwanted traffic from entering a VPC, you can create a NAT gateway that enables instances in a private subnet to initiate outbound traffic but prevents receipt of inbound traffic from the internet.
- Logging via Network Flow Logs: Network Flow Logs is a feature that captures information about the network traffic going to and from network interfaces in a VPC. Flow logs can be used to help monitor the traffic that is going across the network. All three main cloud service providers have Network Flow Logs capabilities. For illustration purposes, in AWS, navigate to VPCs, select your VPC, and click on the Flow logs tab, as seen in Figure 4.42. Alternatively, you can view the logs in Amazon CloudWatch Logs:
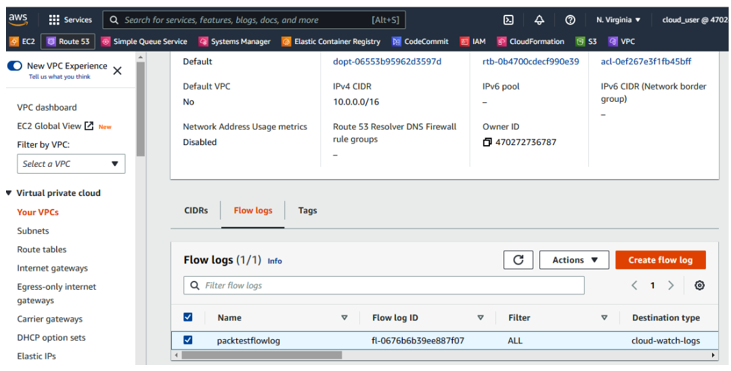
Figure 4.42 – AWS VPC – Flow logs
In this section, we reviewed some techniques to secure data in the cloud. This includes implementing core security controls to mitigate the risks presented by the cloud.
Summary
In this chapter, we looked at network security controls for the three major cloud providers: AWS, Azure, and GCP. We covered how to identify the security control center within each cloud service provider portal and functionality, as well as how to implement industry-standard security benchmarks within security policies. In addition, we also learned how to examine data security controls.
In the next chapter, we’ll review financial resources and change management.