To get a snapshot of the AWS security posture, we can use AWS Security Hub. According to the AWS documentation, “AWS Security Hub is a cloud security posture management service that performs security best practice checks, aggregates alerts, and enables automated remediation.”
To use AWS Security Hub, we first have to enable the service. We can simply search for the service using the AWS search function, as seen in Figure 6.3:
Figure 6.3 – AWS Security Hub
Before you can enable Security Hub standards and controls, you must first enable AWS Config, as seen in Figure 6.4:
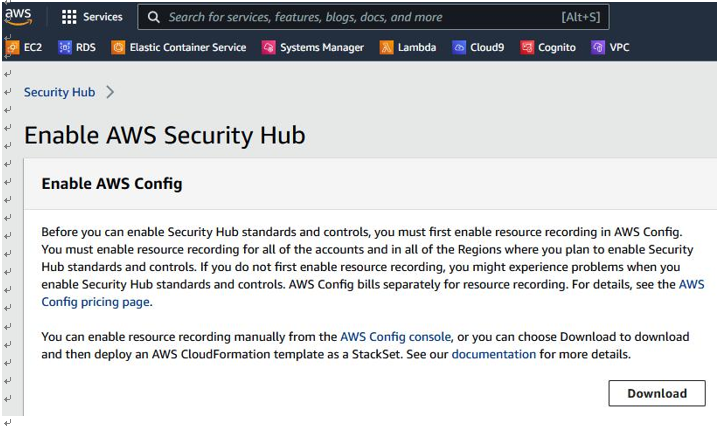
Figure 6.4 – Enabling AWS Config
To enable AWS Security Hub, select the security standards you would like it to perform security checks against as seen in Figure 6.5. AWS Security Hub security checks are currently mapped to AWS Foundational Security Best Practices, the CIS AWS Foundation Benchmark, and Payment Card Industry Data Security Standard (PCI DSS).
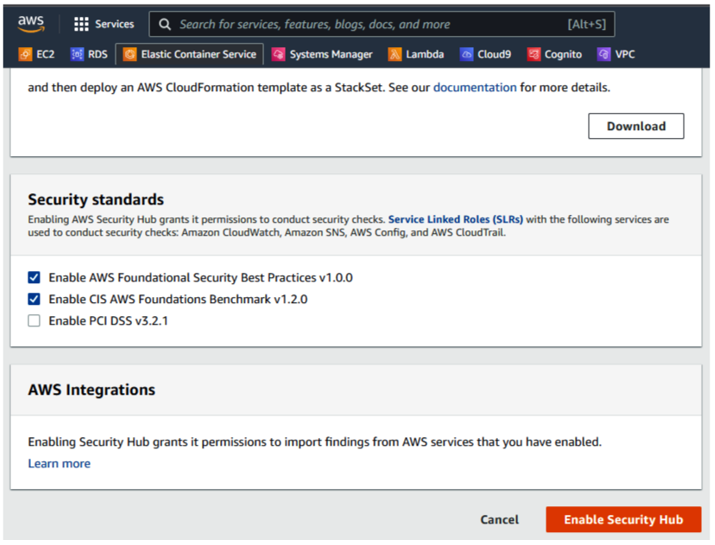
Figure 6.5 – Security standards
Once you have enabled Security Hub, you may have to wait up to two hours for it to populate. There are three important tabs for the IT auditor to review:
- Summary
- Findings
- Insights
Let’s start by reviewing the Summary tab. It has different information such as security standards passed and failed, Resources with the most failed security checks, findings by region, and so on:
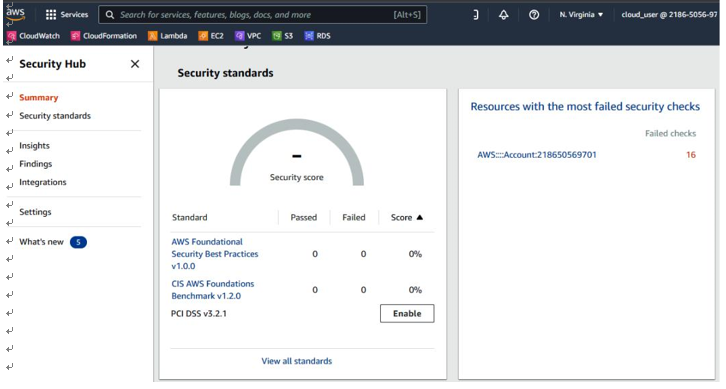
Figure 6.6 – The Summary tab
You can view findings across multiple regions, as seen in Figure 6.7. As you can see, we have 1 moderate finding and 15 low findings:
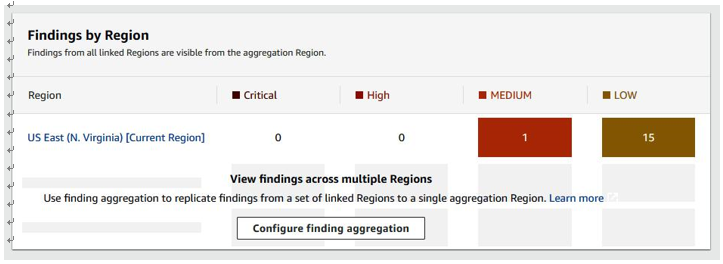
Figure 6.7 – Findings by region
Another tab the IT auditor should review in AWS Security Hub is the Findings tab. Here, you can get the details of a finding and what security checks it failed, as seen in Figure 6.8:
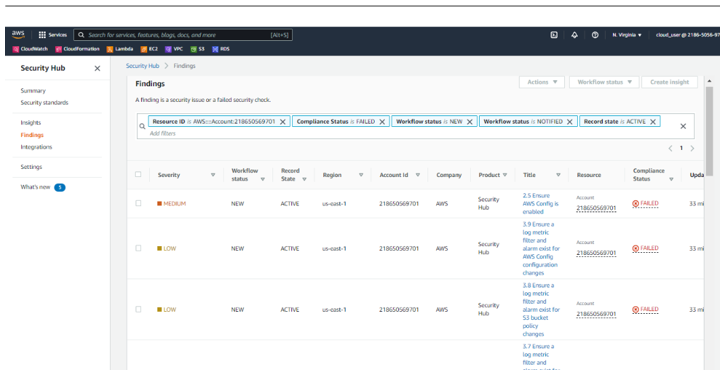
Figure 6.8 – Findings
Another useful tab the IT auditor should review in AWS Security Hub is the Insights tab. Here, you can get insight into the type of finding. The information presented on this tab include: AWS resources with the most findings, S3 buckets with public write or read permissions, AMIs that are generating the most findings, and so on, as seen in Figure 6.9:
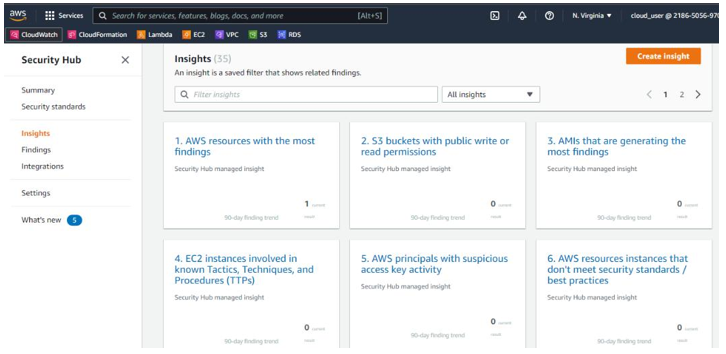
Figure 6.9 – The Insights tab
The second tool an IT auditor should leverage is AWS Config. As per the AWS documentation, “AWS Config is a service that enables you to assess, audit, and evaluate the configurations of your AWS resource.” AWS Config provides AWS-managed rules, which are predefined, customizable rules thatAWS Config uses to evaluate whether your AWS resources align with prescribed best practices. AWS Config can be quite valuable to an IT auditor as the service lets you define your own rules. To get to AWS Config, search for it on the AWS console, as seen in Figure 6.10:
Figure 6.10 – AWS Config search
You can enable AWS Config with 1-click setup, as shown in Figure 6.11:
Figure 6.11 – Enabling AWS Config
Select General settings | Rules, then click Confirm, as seen in Figure 6.12:
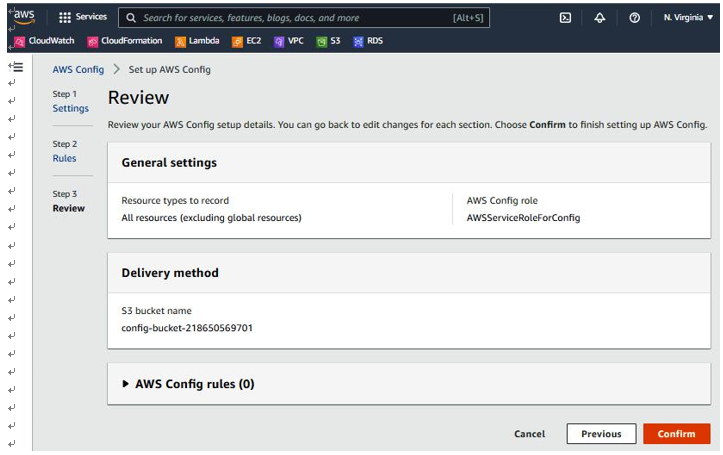
Figure 6.12 – Setting up AWS Config
Once AWS Config has launched, the three most valuable tabs for an IT auditor are the Dashboard, Rules, and Resources tabs. In the Dashboard tab, you can find information such as Configuration Items, Compliance status, and AWS Config success metrics, as seen in Figure 6.13:
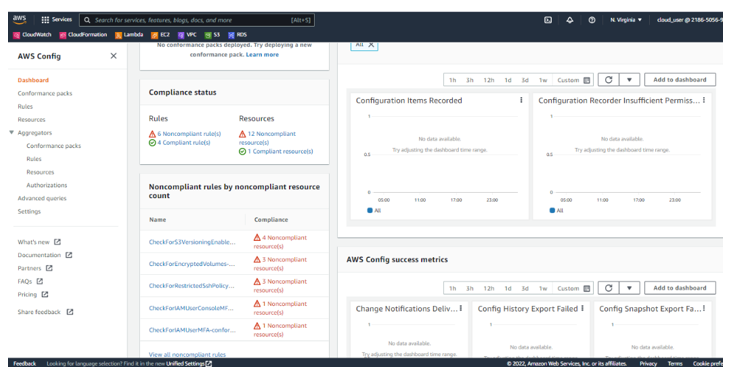
Figure 6.13 – The Dashboard tab
The Rules tab displays whether your resource configurations align with the relevant rules identified, as seen in Figure 6.14:
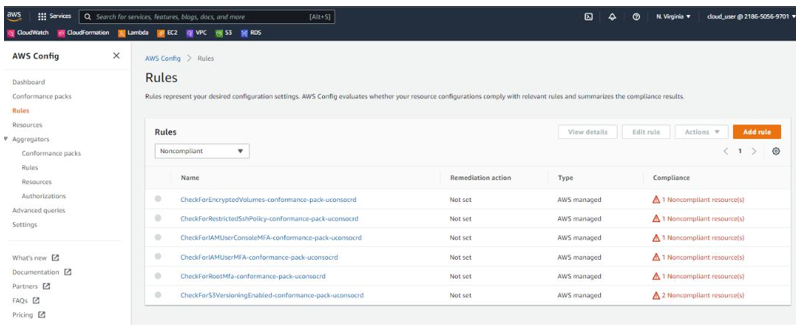
Figure 6.14 – The Rules tab
The Resources tab displays an inventory of supported resources and their compliance status, as shown in Figure 6.15:
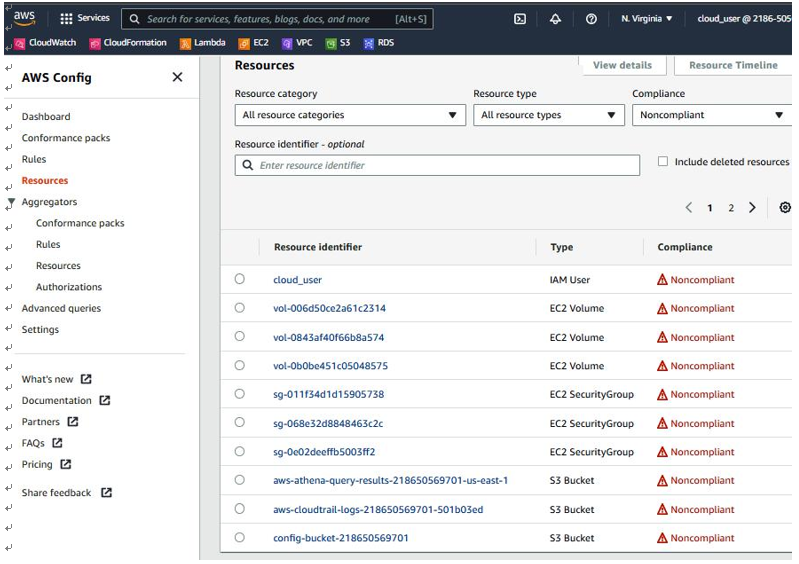
Figure 6.15 – The Resources tab
In our example, you can see we have the IAM User, EC2 Volume, and S3 Bucket types that are Noncompliant. You can click on each resource identifier for more information. The IT auditor would have to investigate relevant findings and collaborate with the cloud customer to come up with appropriate remediation.
A third useful tool for an IT auditor is AWS Trusted Advisor.