Overly permissive access
Cloud environments usually include both human and non-human identities. Cloud environments are often created with overly broad permissions that allow unregulated access to cloud resources. Threat actors who have managed to get initial entry into a cloud environment might be able to leverage these broad permissions to escalate access and move laterally inside the cloud infrastructure.
Identity access management ( IAM) is a framework of policies, processes, and technologies that enable organizations to manage digital identities and control user access to an organization’s data.
Some practices an IT auditor should look out for ways to minimize access risks are as follows:
- Implementing IAM wherever feasible
- Utilizing role-based access control and the least privilege principle
- Enabling multi-factor authentication
- Performing regular reviews of all identity roles and policies
Now that we’ve looked at the common pitfalls organization face in cloud adoption, let’s look at tips and tricks to perform an effective audit.
Tips, tricks, and techniques
Cloud environments are complex and have low visibility. In a traditional data center, there was a finite number of assets that IT auditors could examine and report on. However, in a cloud environment, there can be exponential growth in the number of assets, which may include virtual machines (VMs), virtual networks, containers, serverless functions, and so on. It can be very challenging to inventory what is running in an organization’s cloud.
Asset inventory plays such a foundational role in a cyber security program, that CIS Critical Security Controls and the NIST Cybersecurity Framework list the need to inventory and control infrastructure assets as their first security controls.
The first thing the IT auditor needs to do is to understand the cloud asset inventory to be able to perform an effective audit. The IT auditor needs to understand what applications are running within the cloud and whether they are approved by the organization, or if they represent shadow IT. In this section, we will demonstrate how to leverage native tools from each cloud service provider to get inventory and a quick snapshot security posture of the cloud environment.
It is important to note that the tips and tricks provided in this chapter should be incorporated and aligned based on the cloud customer’s cloud security policies, standards, and procedures.
AWS
In AWS, you can use the AWS Tag Manager to inventory cloud resources. AWS allows you to assign metadata to a cloud customer’s AWS resources using tags. All tags serve as simple labels that consist of a user-defined key and an optional value. The Tag Editor can be found under AWS Resource Groups. To list all resources using the Tag Editor, you can either manually select specific regions, or all of the regions listed under Region by selecting All supported resource types, and not specifying a tag. Then, click Find resources and this will show all resources that were created, as shown in Figure 6.1:
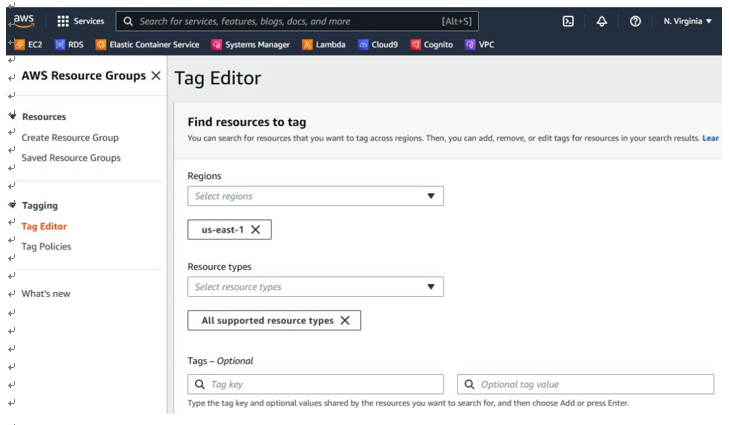
Figure 6.1 – Finding resources to tag
All the resources are identified, as shown in Figure 6.2:
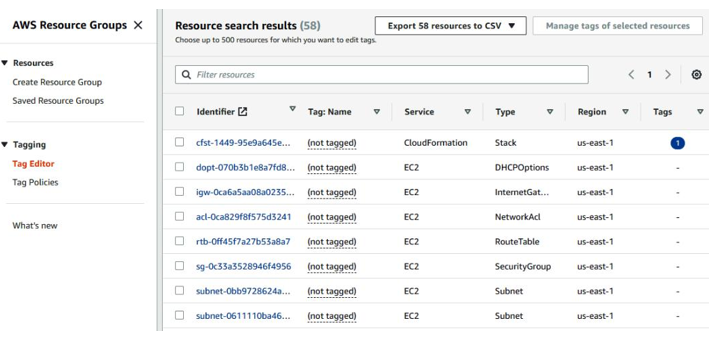
Figure 6.2 – Resource search results